10 Examples of How Content Creators and Teams Are Using AI
Buffer Social
JULY 31, 2023
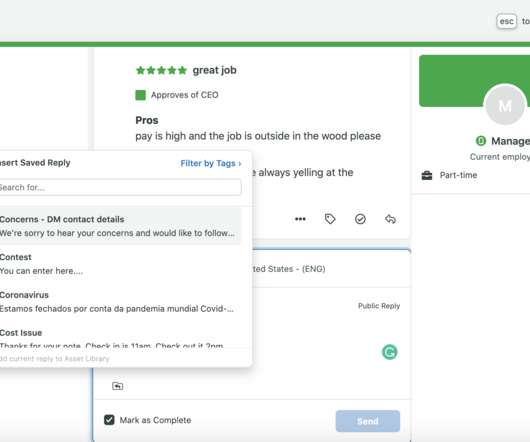
To help make the process a bit easier, we put together a list of examples from different creators and content teams about their policies regarding using AI in content creation. Example of a CNET AI disclaimer The tech publication now updates an AI Policy page detailing how they’re using AI.
























Let's personalize your content