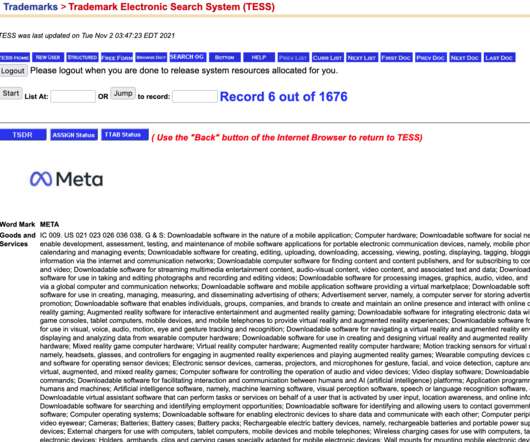
Facebook Filed for a Trademark on the Word Meta. You Should See the Description.
Bill Hartzer
NOVEMBER 2, 2021
G & S: Downloadable software in the nature of a mobile application; Computer hardware; Downloadable software for social networking and creating and interacting with online communities; Downloadable software for creating, managing and accessing groups within virtual communities; Software development tools; Downloadable software to enable development, (..)












Let's personalize your content