The Feud Over Apple Privacy Label – Tech-Giants Don’t Like It
Tweaklibrary
MARCH 20, 2021
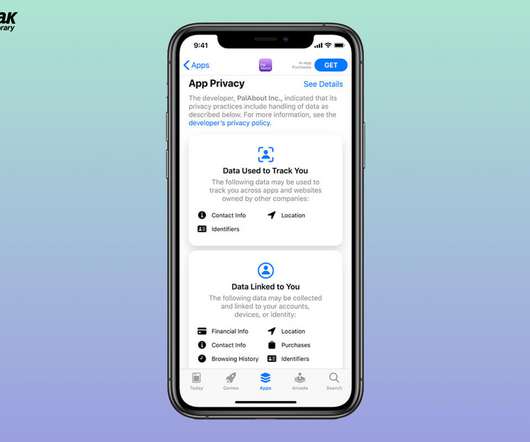
Apple did it in a somewhat exciting fashion – Apple Privacy Labels. Though the companies do explain about all the data they take in their Privacy policy but let’s be reasonable, who reads that? Now looking at the Privacy labels, Isn’t it much easier this way to be aware of the privacy policy and software’s intrusion in your lives?

















Let's personalize your content