How to Hide your IP Address? 4 Different Methods (Free and Paid)
Tweaklibrary
SEPTEMBER 24, 2020
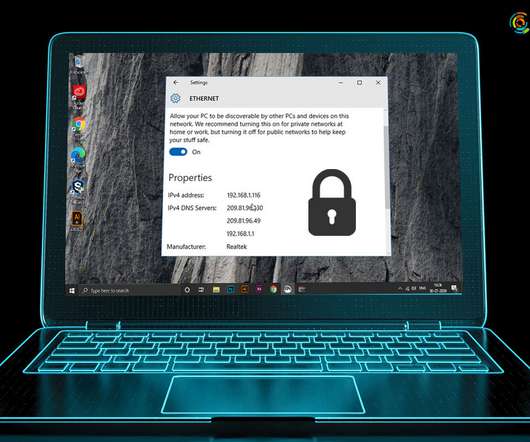
One should always take measures to hide IP addresses in order to protect online privacy. How to hide your IP Address to protect our online privacy? But we have accumulated four best techniques through which you can easily hide your IP to protect your online privacy. It also offers considerable protection to your online privacy.














Let's personalize your content